Create Filters to Assign Apps, Policies, and Profiles in Microsoft Intune
Filters, not just for social media anymore.
Microsoft Intune provides a comprehensive set of tools for managing devices and applications. One of the features of Intune is filters, which are used to assign policies, apps, and profiles to devices based on the rules you create. Filters allow you to narrow the assignment scope of a policy and dynamically target devices based on device properties you enter.
The following attributes can be used to either include or exclude devices from an assignment:
- Device Name
- Manufacturer
- Model
- Device Category
- OS Version
- IsRooted
- Device Ownership
- Enrolment Profile Name
- Operating System SKU
But like how does it work, man?
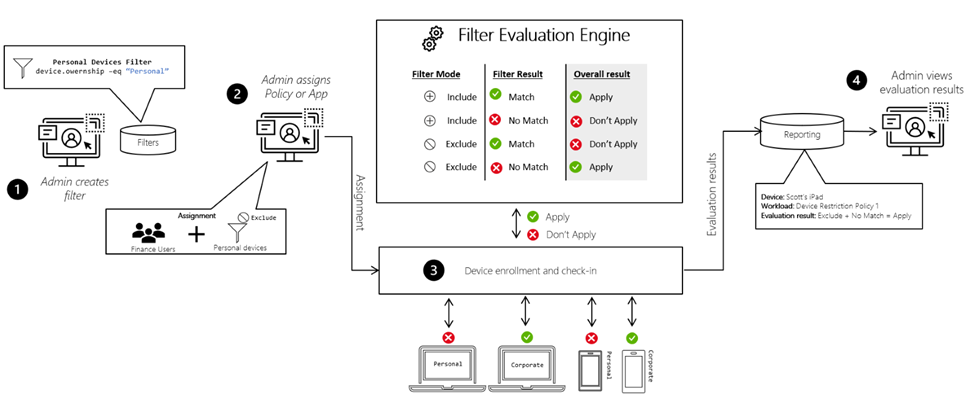
Filters dynamically assess applicability of policies on devices. Here's an overview based on the image above:
First, you create a filter that is reusable for any platform based on specific device properties, such as personal devices.
Next, you assign a policy or app to a group and include or exclude the filter in the assignment. For instance, you may choose to include personal devices or exclude them from the policy.
The filter is evaluated when a device enrolls, checks in with the Intune service, or when a policy evaluation occurs.
Finally, you can view the filter results based on the evaluation, such as whether the app or policy applies or not.
Here are some examples of how you can use filters:
- Deploy a Windows device restriction policy to only the corporate devices in the Marketing department while excluding personal devices.
- Deploy an iOS/iPadOS app to only the iPad devices in the Finance users group.
- Deploy an Android mobile phone compliance policy to all users in the company, and exclude Android meeting room devices that don't support the mobile phone compliance policy settings.
Filters are available for Android device administrator, Android Enterprise, iOS/iPadOS, macOS, and Windows 10/11.
Before a policy is applied to a device, filters dynamically evaluate applicability. Filters can be evaluated when the device enrolls, checks in with the Intune service, or at any other time a policy evaluates.
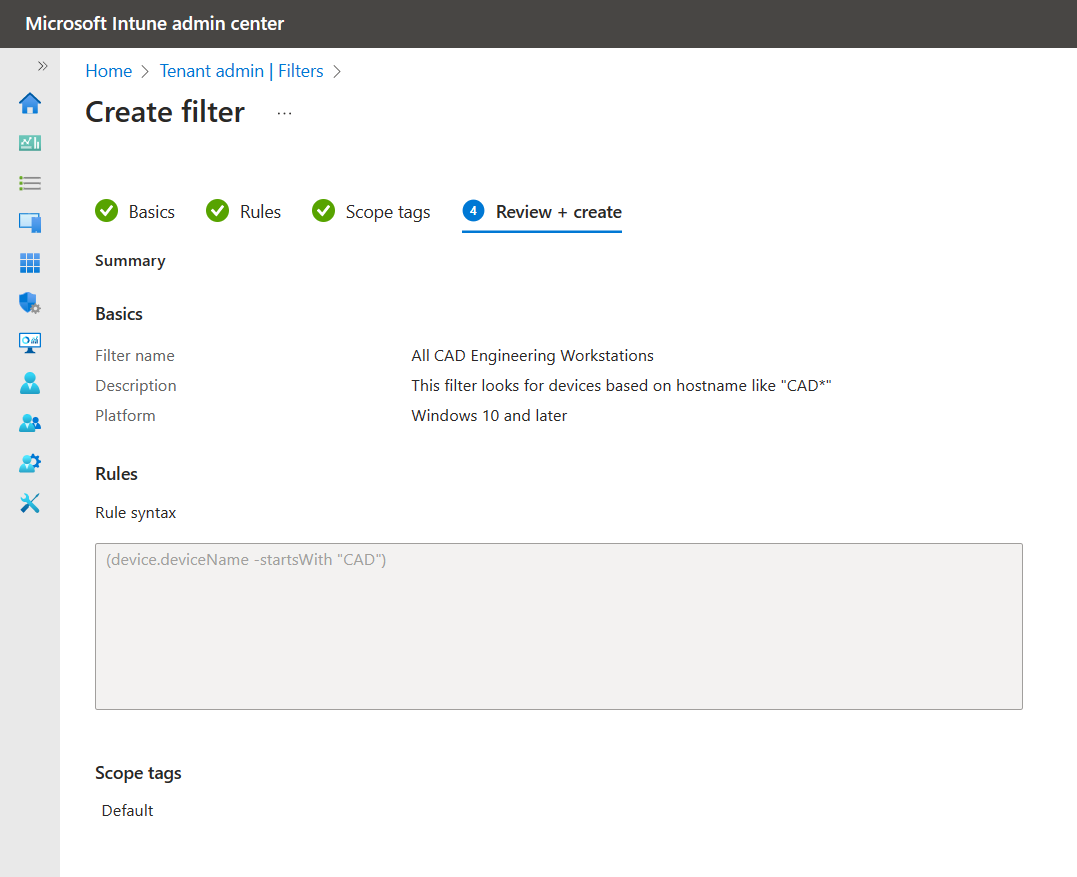
To create a filter in Intune, follow these steps:
- Sign in to the Microsoft Intune admin center.
- Select Tenant administration > Filters > Create.
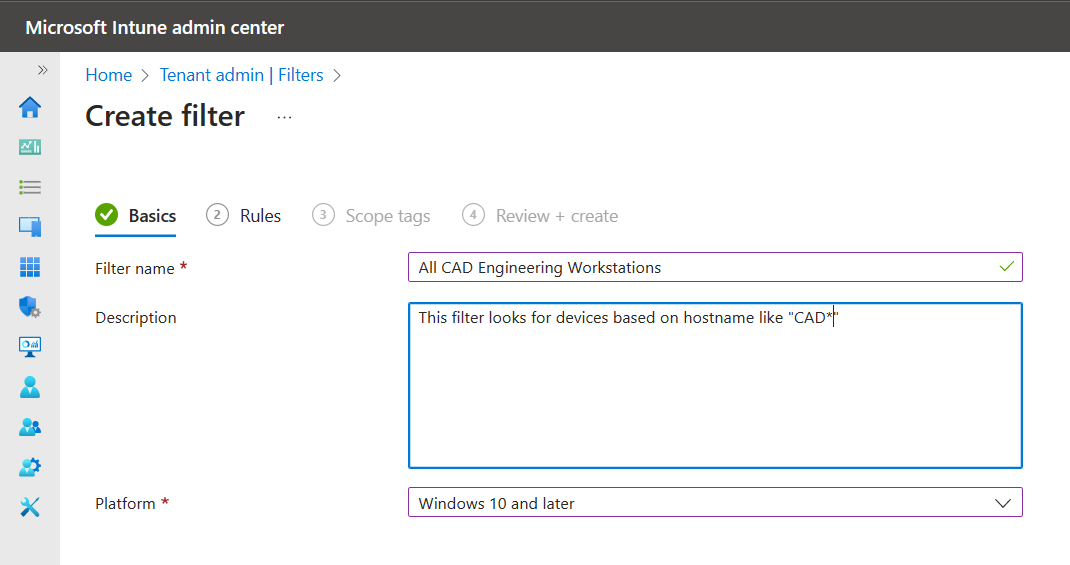
- In Basics, enter the following properties:
- Filter name: Enter a descriptive name for the filter.
- Description: Enter a description for the filter. This setting is optional but recommended.
- Platform: Select your platform.
4. In Rules, there are two ways to create a rule: Use the rule builder or use the rule syntax.
The rule builder allows you to select a property for your rule, such as device or operating system SKU, select the operator from the list, such as equals or contains, and enter the value in your expression.
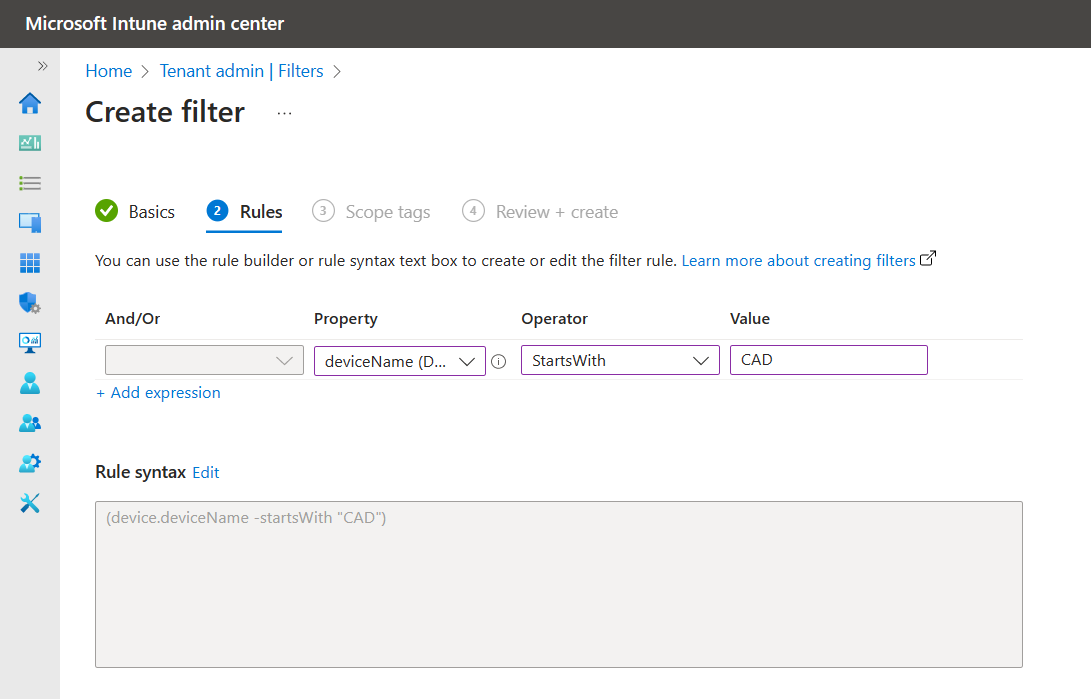
The rule syntax editor (accessible by clicking edit next to 'Rule syntax') allows you to manually enter your rule expression, such as (device.osVersion -eq "10.0.18362") and (device.manufacturer -eq "Microsoft").
5. Assign any relevant scope tags
6. Review and create
Select Preview devices to see a list of enrolled devices that match your filter criteria. In this list, you can also search for devices by device name, OS version, device model, device manufacturer, the user principal name of the primary user, and device ID.
Device Properties
You can use the following device properties in your filter rules:
Device Name
Create a filter rule based on the Intune device name property. Enter a string value for the device's full name (using -eq, -ne, -in, -notIn operators), or partial value (using -startswith, -contains, -notcontains operators).
Examples:
(device.deviceName -eq "Jorge's Device")(device.deviceName -in ["Jorge's device", "Jon's device"])(device.deviceName -startsWith "J")Manufacturer
Create a filter rule based on the Intune device manufacturer property. Enter the full string value (using -eq, -ne, -in, -notIn operators), or partial value (using -startswith, -contains, -notcontains operators).
Examples:
(device.manufacturer -eq "Microsoft")(device.manufacturer -startsWith "mac")Model
Create a filter rule based on the Intune device model property. Enter the full string value (using -eq, -ne, -in, -notIn operators), or partial value (using -startswith, -contains, -notcontains operators).
Examples:
(device.model -eq "Surface Book 3")(device.model -in ["Surface Book 3", "Surface Book 2"])(device.model -startsWith "Surface Book")Device Category
Create a filter rule based on the Intune device category property. Enter the full string value (using -eq, -ne, -in, -notIn operators), or partial value (using -startswith, -contains, -notcontains operators).
Examples:
(device.deviceCategory -eq "Engineering devices")(device.deviceCategory -contains "Engineering")(device.model -startsWith "E")OS Version
Create a filter rule based on the Intune device operating system (OS) version. Enter the full string value (using -eq, -ne, -in, -notIn operators), or partial value (using -startswith, -contains, -notcontains operators).
Examples:
(device.osVersion -eq "14.2.1")(device.osVersion -startsWith "10.0.18362")Note:
For Apple devices, the OSversion property doesn't include Apple's Security Patch Version (SPV) information. The SPV is the letter after the version number, like 14.1.2a. When creating filters for Apple devices, don't include the SPV in the OSversion rule syntax.
Rooted or Jailbroken Devices
Create a filter rule based on the device's rooted (Android) or jailbroken (iOS/iPadOS) device property. Select True, False, or unknown values using the -eq and -ne operators.
Example:
(device.isRooted -eq "True")Device Ownership
Create a filter rule based on the device's ownership property in Intune. Select Personal, Corporate, or unknown values using the -eq and -ne operators.
Example:
(device.deviceOwnership -eq "Personal")Enrollment Profile
Create a filter rule based on the enrollment profile name. This property is applied to a device when the device enrolls. It's a string value created by you, and matches the Windows Autopilot, Apple Automated Device Enrollment (ADE), or Google enrollment profile applied to the device. To see your enrollment profile names, sign in to the Intune admin center, and go to Devices > Enroll devices.
Enter the full string value (using -eq, -ne, -in, -notIn operators), or partial value (using -startswith, -contains, -notcontains operators).
Examples:
(device.enrollmentProfileName -eq "DEP iPhones")(device.enrollmentProfileName -startsWith "Autopilot Profile")(device.enrollmentProfileName -ne $null)Azure AD Join type
Create a filter rule based on the device's Azure AD Join type. Choose between Azure AD Join, Hybrid Azure AD, Azure AD registered or unknown values (with -eq, -ne, -in, -notIn operators).
Examples:
(device.deviceTrustType -eq "Azure AD joined")(device.deviceTrustType -ne "Azure AD registered")(device.deviceTrustType -in ["Hybrid Azure AD joined","Azure AD joined"])Operating System SKU
Create a filter rule based on the device's Windows client OS SKU. Enter the full string value (using -eq, -ne, -in, -notIn operators), or partial value (using -startswith, -contains, -notcontains operators).
Examples:
(device.operatingSystemSKU -eq "Enterprise")(device.operatingSystemSKU -in ["Enterprise", "EnterpriseS", "EnterpriseN", "EnterpriseEval"])(device.operatingSystemSKU -startsWith "Enterprise")Get-WmiObject -Class Win32_OperatingSystem | select operatingsystemSKUAdvanced rule editing
When you create a filter, you can manually create simple or complex rules in the rule syntax editor. You can also use common operators, such as or, contains, and more. The format is similar Azure AD dynamic groups: ([entity].[property name] [operation] [value]).
What you need to know
- The properties, operations, and values are case insensitive.
- Parentheses and nested parentheses are supported.
- You can use
Nullor$Nullas a value with the-Equalsand-NotEqualsoperators. - Some advanced syntax options, such as nested parentheses, are only available in the rule syntax editor. If you use advanced expressions in the rule syntax editor, then the rule builder is disabled.
Supported operators
You can use the following operators in the rule syntax editor:
Or: Use for all value types, especially when grouping simple rules.
- Allowed values:
-or|or - Example:
(device.manufacturer -eq "Samsung") or (device.model -contains "Galaxy Note")
And: Use for all value types, especially when grouping simple rules.
- Allowed values:
-and|and - Example:
(device.manufacturer -eq "Samsung") and (device.model -contains "Galaxy Note")
Equals: Use for all value types, including simple rules, strings, arrays, and more.
- Allowed values:
-eq|eq - Example:
(device.manufacturer -eq "Samsung") and (device.model -eq "Galaxy Note")
NotEquals: Use for all value types, including simple rules, strings, arrays, and more.
- Allowed values:
-ne|ne - Example:
(device.manufacturer -ne "Samsung") or (device.model -ne "Galaxy Note")
StartsWith: Use for string value types.
- Allowed values:
-startsWith|startsWith - Example:
(device.manufacturer -startsWith "Sams")
In: Use for array value types, such as ["1", "2"].
- Allowed values:
-in|in - Example:
(device.manufacturer -in ["Samsung","Lenovo","Microsoft"])
NotIn: Use for array value types, such as ["1", "2"].
- Allowed values:
-notIn|notIn - Example:
(device.manufacturer -notIn ["Samsung","Lenovo","Microsoft"])
Contains: Use for string value types.
- Allowed values:
-contains|contains - Example:
(device.manufacturer -contains "Samsung")
NotContains: Use for string value types.
- Allowed values:
-notContains|notContains - Example:
(device.manufacturer -notContains "Samsung")
Additional example filters
Filter by all Windows 10 and 11 major versions:
(device.osVersion -startsWith "10.0.22")
or (device.osVersion -startsWith "10.0.19043")
or (device.osVersion -startsWith "10.0.19042")
or (device.osVersion -startsWith "10.0.19041")
or (device.osVersion -startsWith "10.0.18363")
or (device.osVersion -startsWith "10.0.18362")
or (device.osVersion -startsWith "10.0.17763")
or (device.osVersion -startsWith "10.0.17134")
or (device.osVersion -startsWith "10.0.16299")
or (device.osVersion -startsWith "10.0.15063")
or (device.osVersion -startsWith "10.0.14393")
or (device.osVersion -startsWith "10.0.10586")
or (device.osVersion -startsWith "10.0.10240")Filter by all Android Enterprise by major Android version release:
Device.osVersion -startswith ("12")
or Device.osVersion -startswith ("11")
or Device.osVersion -startswith ("10")
or Device.osVersion -startswith ("9")
or Device.osVersion -startswith ("8")
or Device.osVersion -startswith ("7")
or Device.osVersion -startswith ("6")
or Device.osVersion -startswith ("5")Filter by all iOS/iPadOS by major version:
Device.osVersion -startswith ("16")
or Device.osVersion -startswith ("15")
or Device.osVersion -startswith ("14")
or Device.osVersion -startswith ("13")
or Device.osVersion -startswith ("12")
or Device.osVersion -startswith ("11")
or Device.osVersion -startswith ("10")
or Device.osVersion -startswith ("9")
or Device.osVersion -startswith ("8")Filter by device model
(device.model -eq "Virtual Machine")Filter by enrollment profile name
(device.enrollmentProfileName -eq "CAD Design")Filter by device manufacturer
(device.manufacturer -eq "LENOVO")These are just a few examples of filter queries you can use with Intune device filters. You can customize these queries based on your specific requirements to filter devices more effectively.
In conclusion, filters are an essential feature of Microsoft Intune that enable IT admins to assign policies, apps, and profiles based on specific criteria. By using filters, you can ensure that your devices are managed efficiently and effectively, saving time and resources.
Recommended additional resources:
I hope this helps.
> Jorgeasaurus